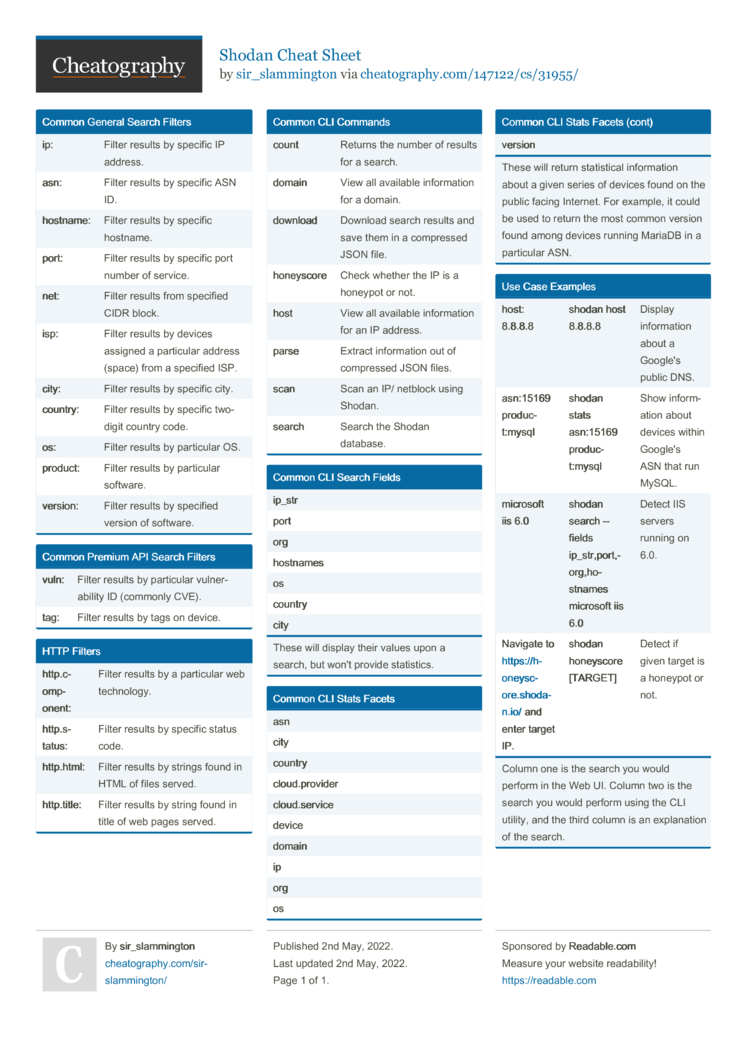
Shodan Cheat Sheet by sir_slammington - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion

Shodan: The Internet Crawler. Finding a Target's Public Assets | by Alex Rodriguez | Geek Culture | Medium
GitHub - TheLeopardsH/Shodan: Filters for Shodan Search engine to find vulnerbilities devices connected to internet





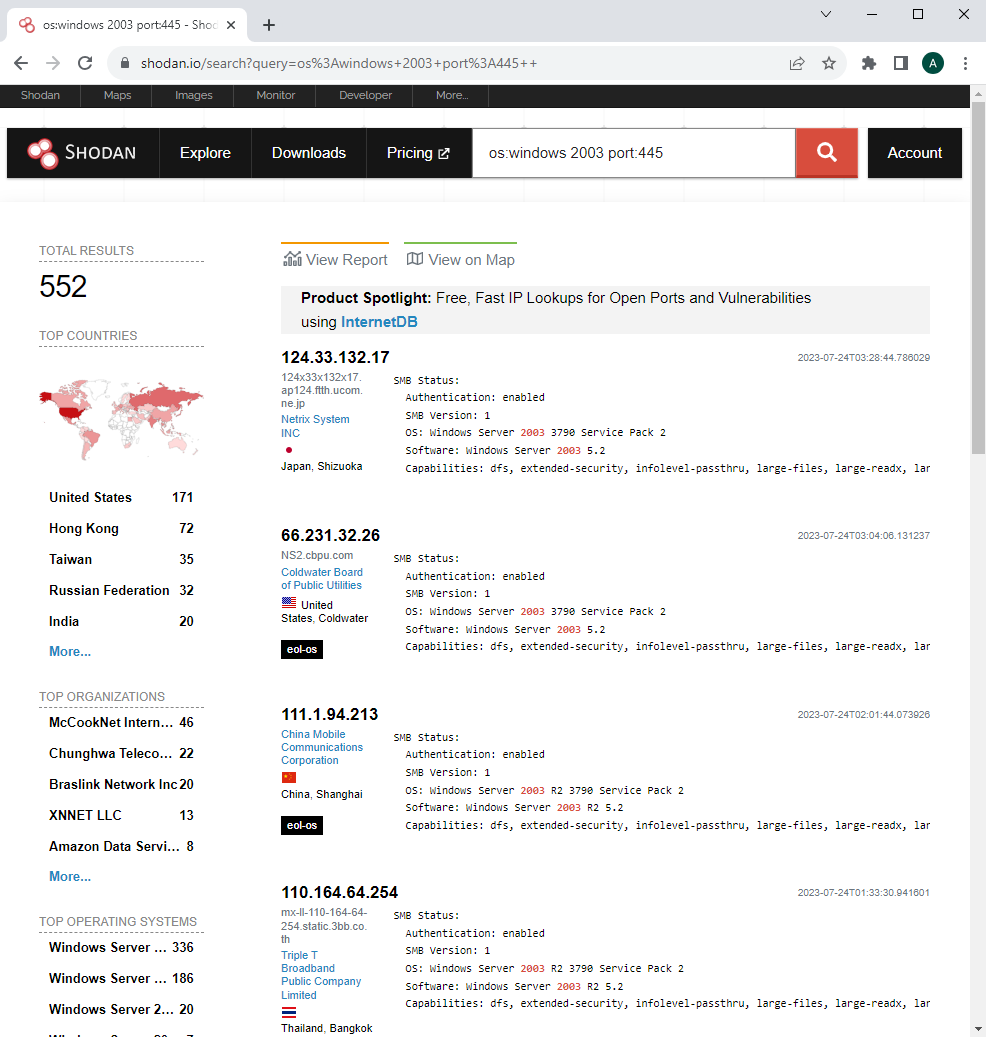
![OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 3 OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 3](https://techofide.com/media/uploads/2023/03/21/5_j3mpfQF.webp)
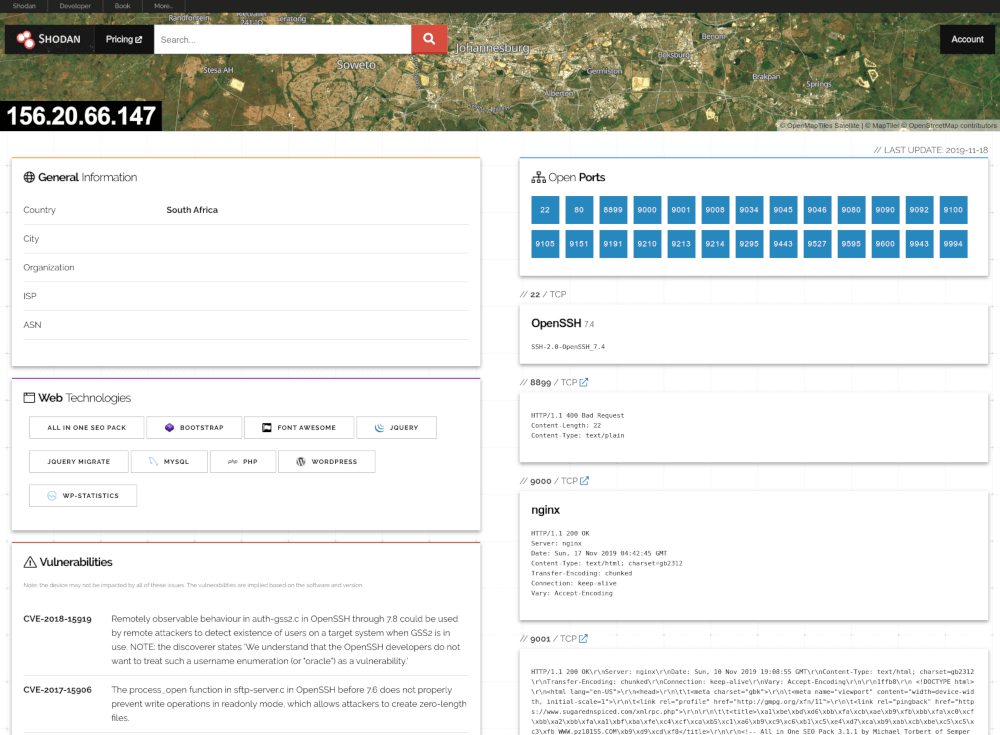


![Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~] Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/wp-content/uploads/2020/03/shodan-vulns.png)