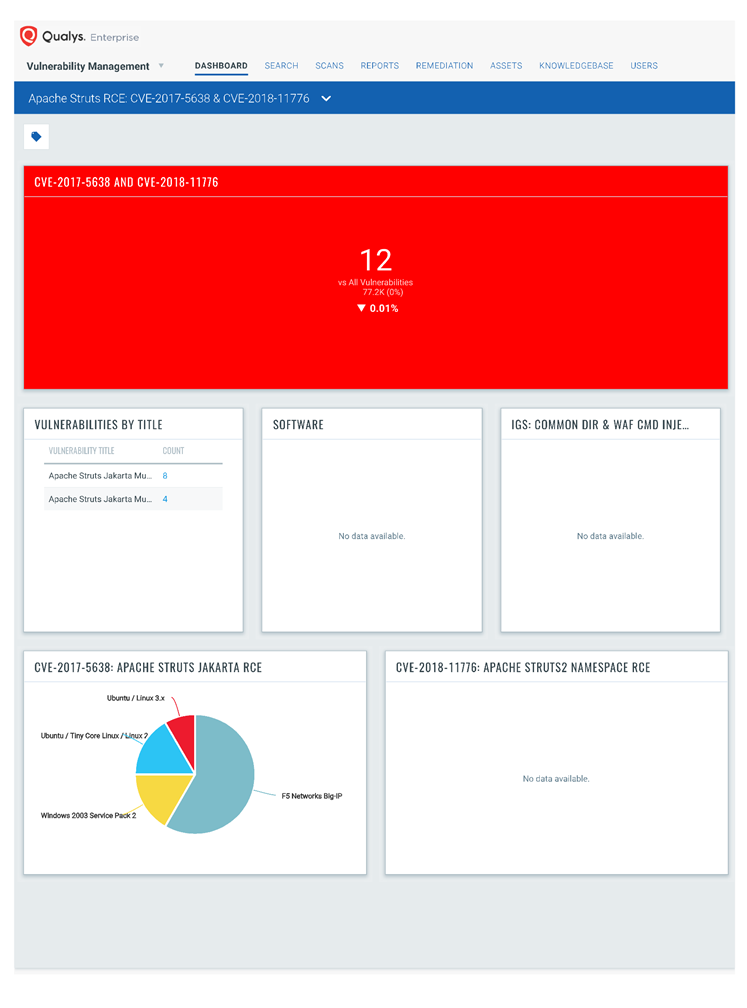
Apache Struts Remote Code Execution Vulnerability Affecting ... - vulnerability database | Vulners.com

Intrusion Policy Report: Modified by Admin Last Modified 2017-01-15 18:56:52 (UTC) | PDF | Domain Name System | Malware

Read: Apache Struts Patches 'Critical Vulnerability' CVE-201... - vulnerability database | Vulners.com

Intrusion Policy Report: Modified by Admin Last Modified 2017-01-15 18:56:52 (UTC) | PDF | Domain Name System | Malware