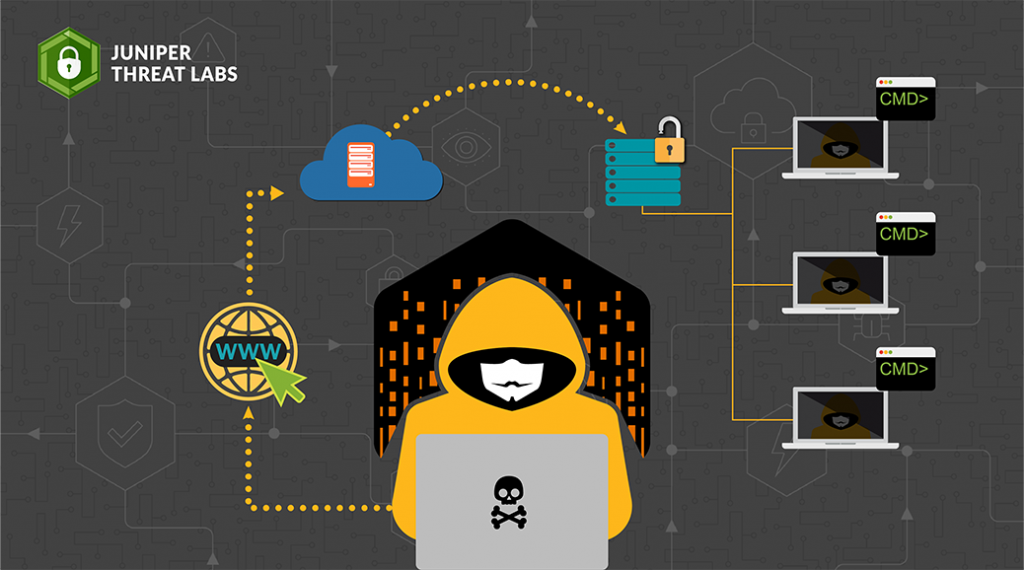
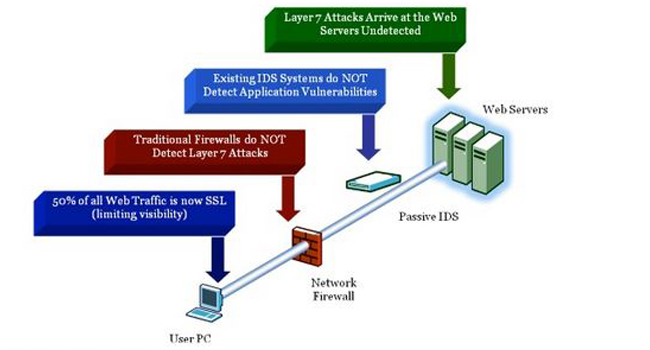
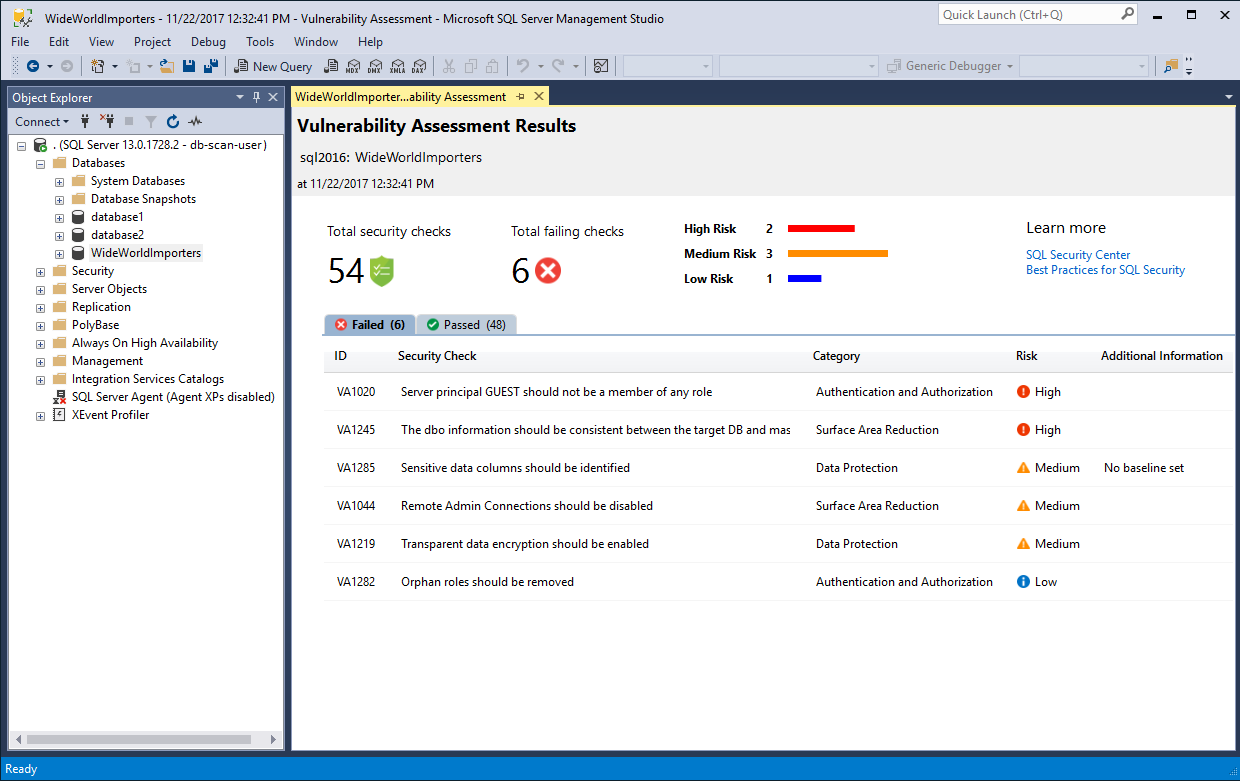
Advisory: Two high-risk vulnerabilities in GoAhead web server - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Vulnerable SDK components lead to supply chain risks in IoT and OT environments | Microsoft Security Blog
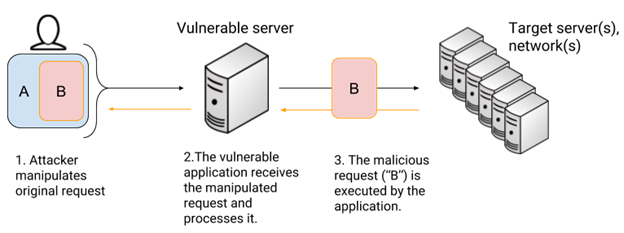
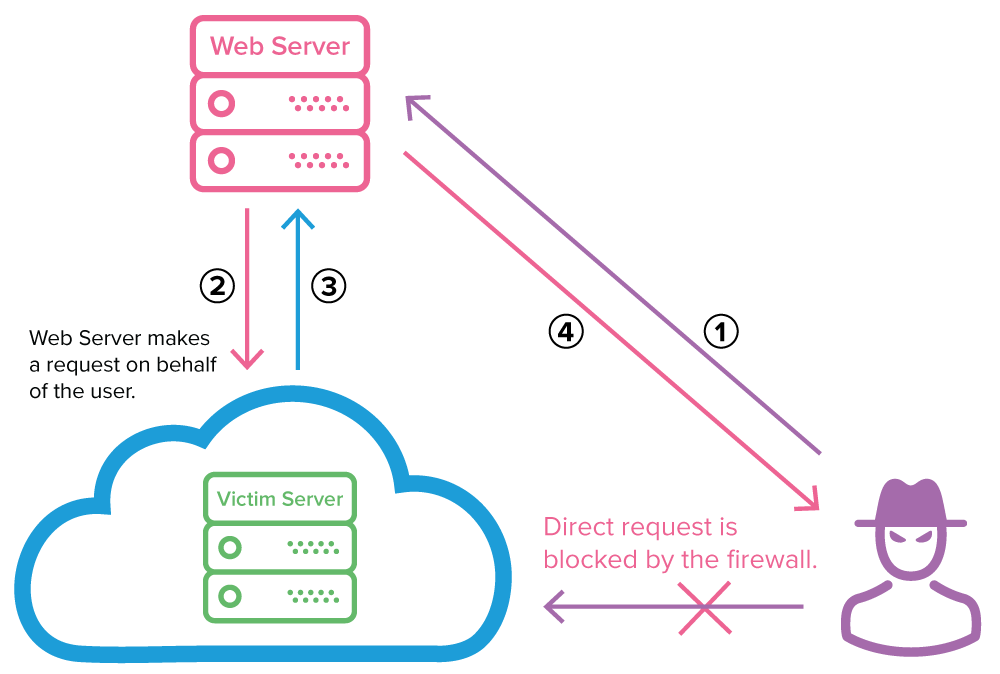
SSRF's up! Real World Server-Side Request Forgery (SSRF) Shorebreak Security - Experts in Information Security Testing

Critical Vulnerabilities in Atlassian Confluence: Zero-Day Exploits targeting CVE-2023-21715, Application Security, and Nation-State Threats - Phoenix Security
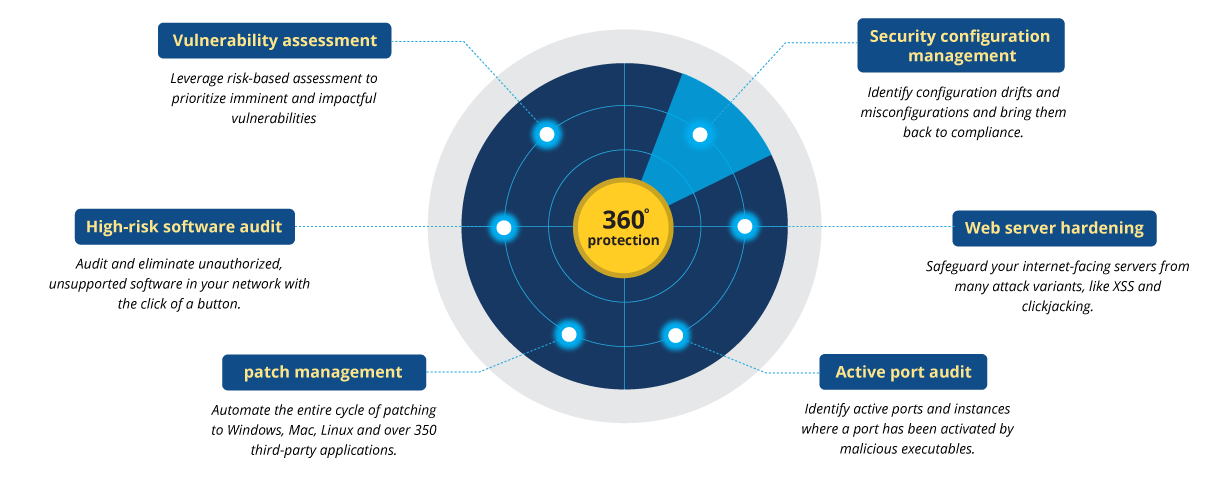
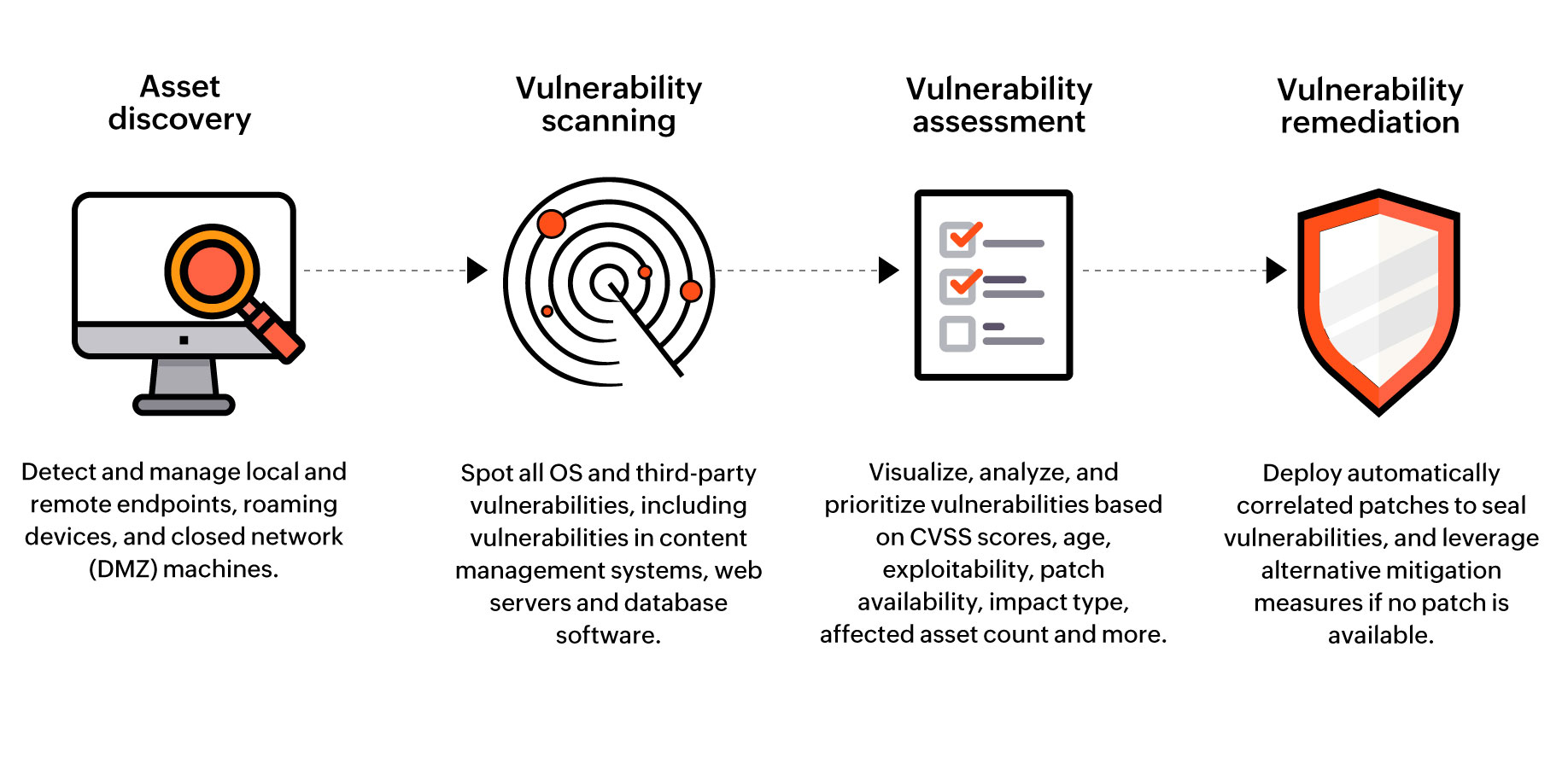
What is vulnerability management? | Vulnerability management process - ManageEngine Vulnerability Manager Plus

ShellTorch: Multiple Critical Vulnerabilities in PyTorch Model Server (TorchServe) (CVSS 9.9, CVSS 9.8) Threatens Countless AI Users